Security Leaders: Your unified view of cyber risk awaits with NodeZero Insights.
Autonomous Security Platform

Security Controls Validation

Hunting

Automated Remediation
Security Data Fabric
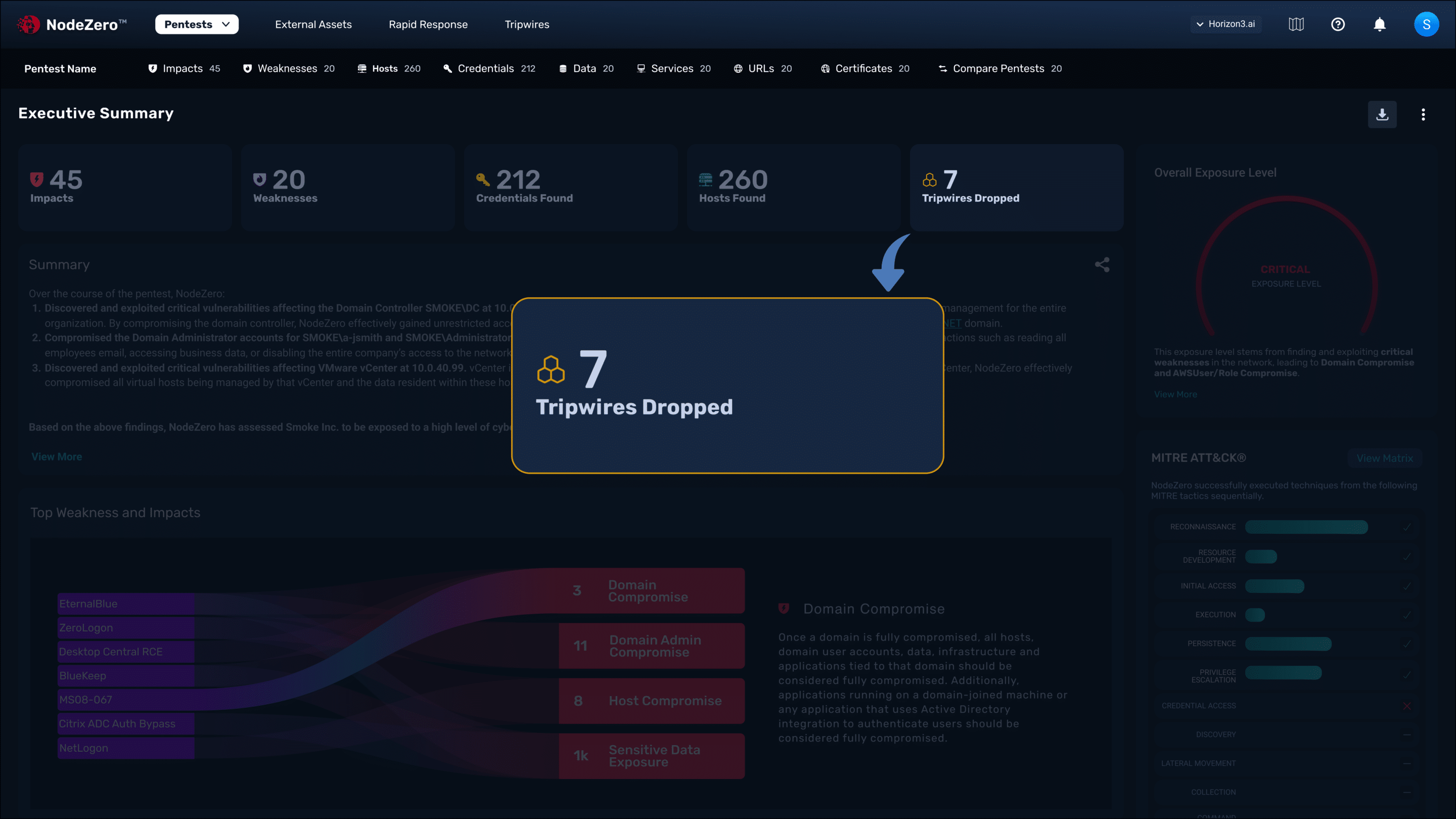
NodeZero Pentest Results
NodeZero Tripwires Early Warning Network
Delivered via
Commercial
SaaS
GDPR Compliant
SaaS
FedRAMP, Secret, Top Secret SaaS
In-Country Data SaaS
We are rated 4.7 ★ on

Autonomous Pentesting with NodeZero
Autonomous Pentesting is licensed as an annual subscription based on the number of unique assets assessed. With that subscription, you can test your entire enterprise as often as you want, instead of a small sample once a year. If you need to run quarterly pentests or more, you’ll save money by shifting to NodeZero.
Here’s what’s included in the subscription:

Infrastructure Attack Surface

Identity Attack Surface

Operational Scenario Testing

Compliance Testing and Reporting

Rapid Response to CISA KEV’s
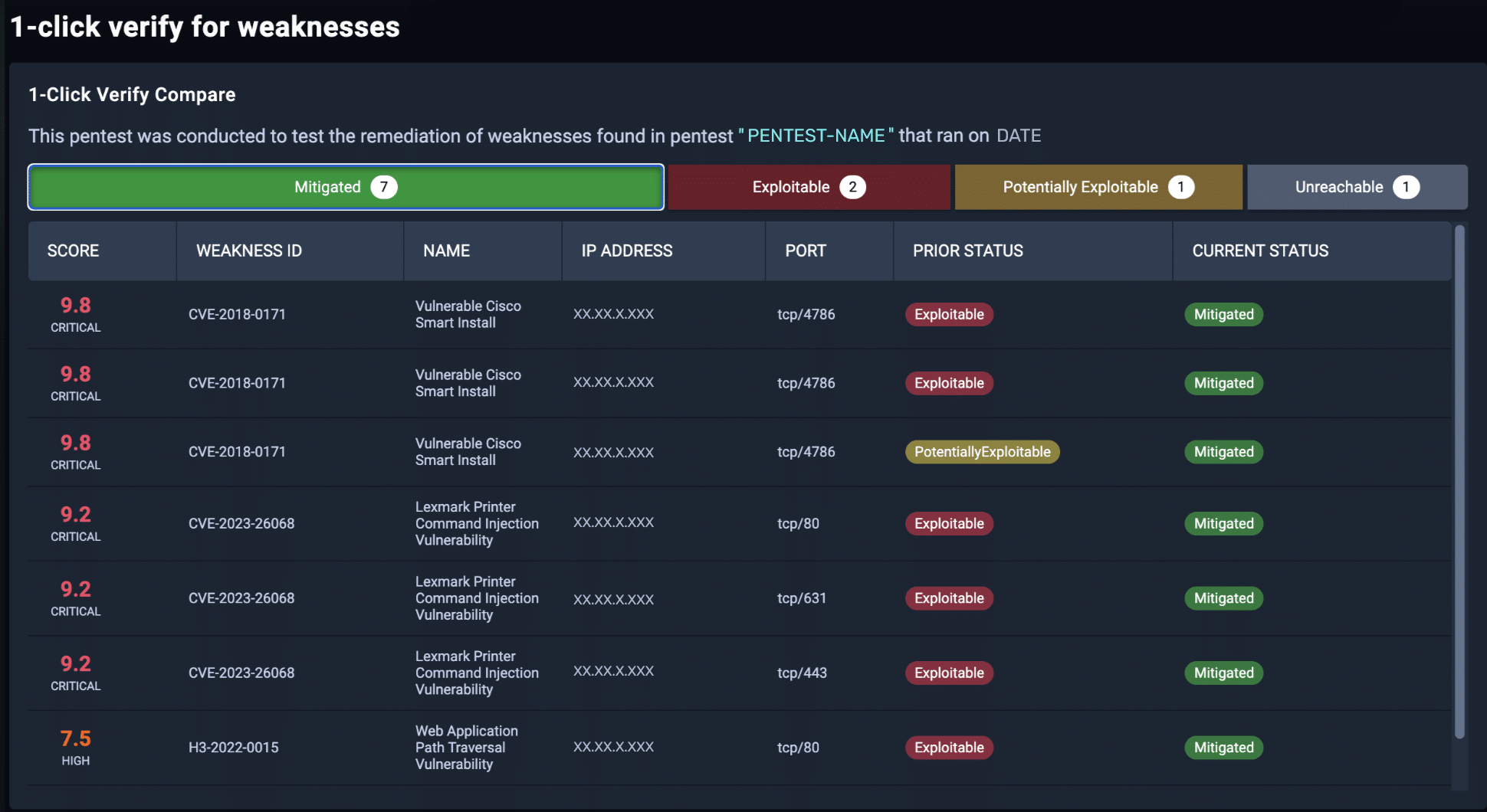
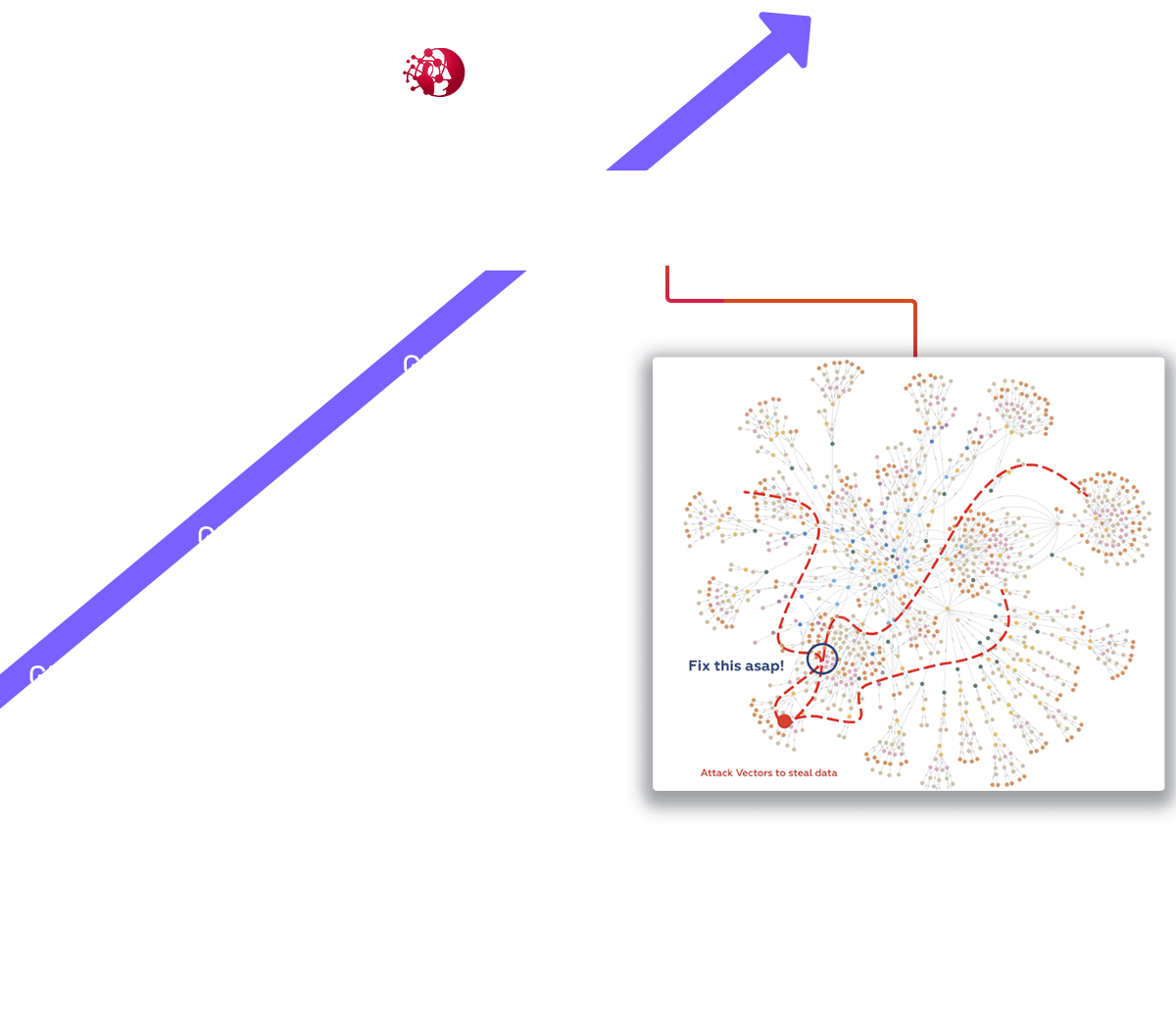
Find and Fix Attack Vectors Before Attackers Can Exploit Them
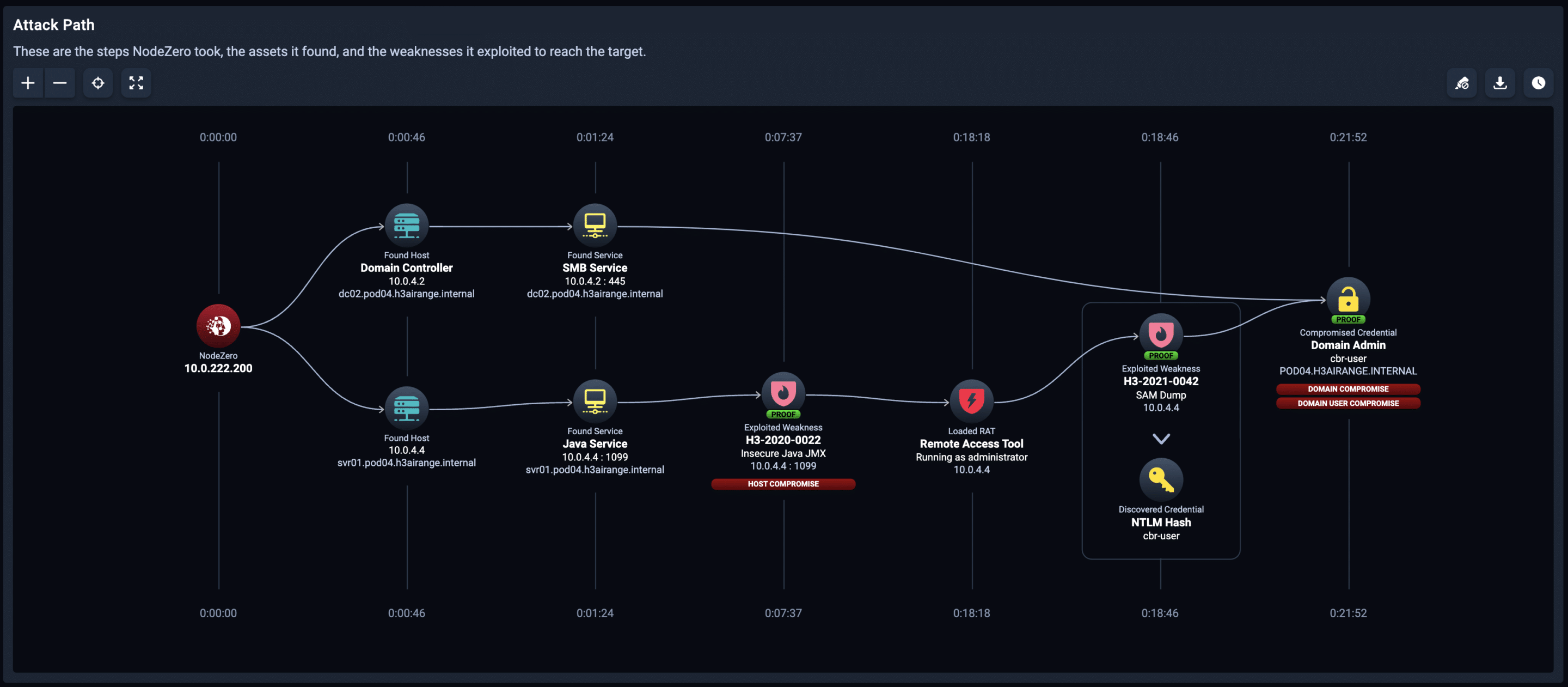
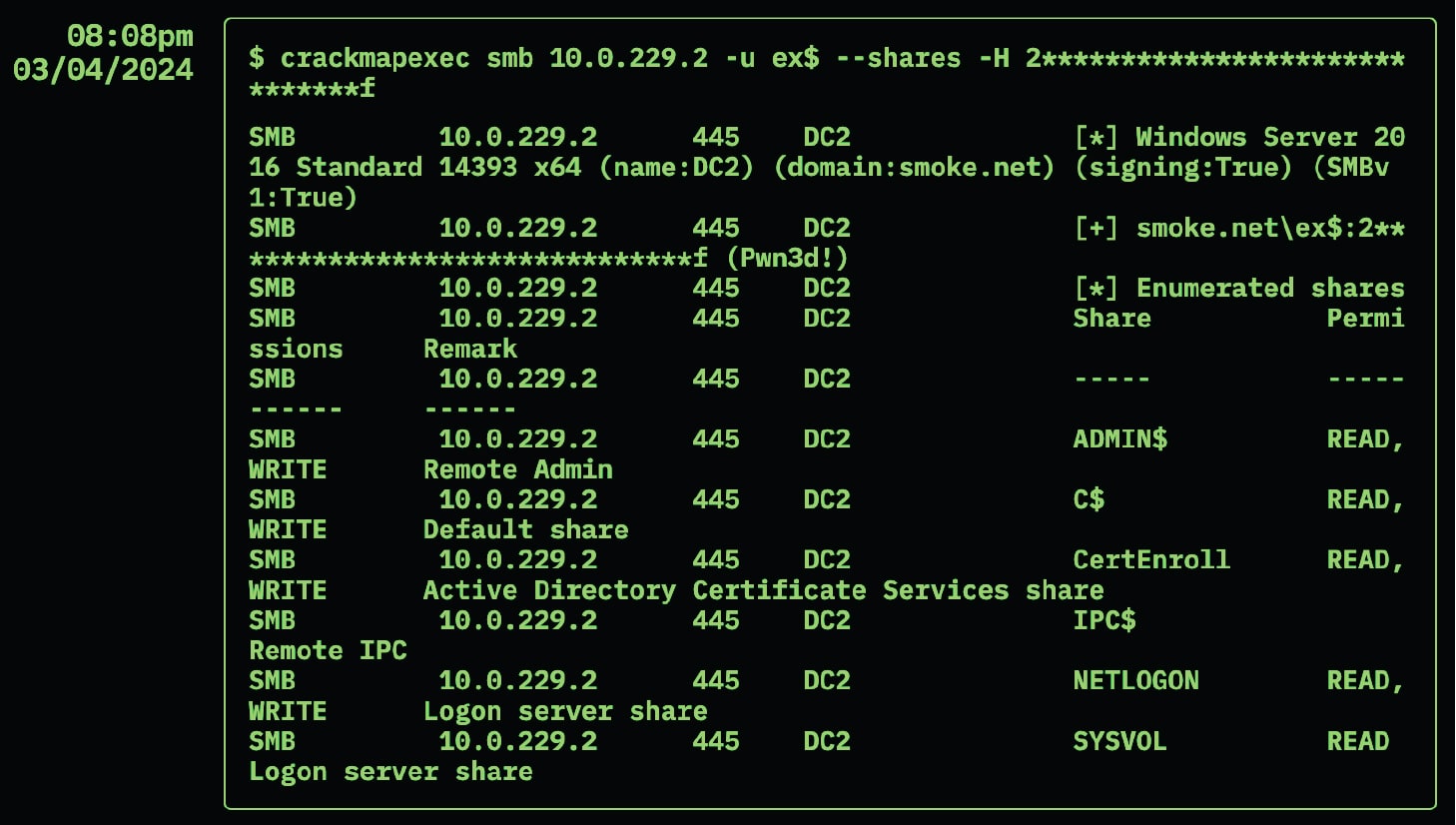
How does NodeZero Do it?


In this autonomous pentest attack path, NodeZero exploited two weaknesses to achieve domain compromise, a Java JMX misconfiguration and SAM credential dumping.
NodeZero will chain together misconfigurations, dangerous product defaults, exploitable CVE's, ineffective security controls, and harvested credentials. You can then see the way NodeZero combined these security issues across hosts together into an easy-to-understand attack path.

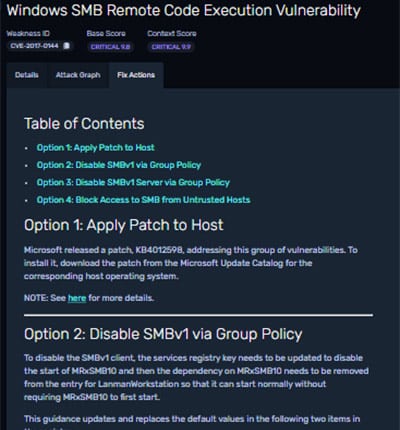
Your team will save time using the detailed remediation guidance for every weakness identified and a complete Fix Action report for your reference, including details on which fixes will solve the most problems, maximizing your return on effort.
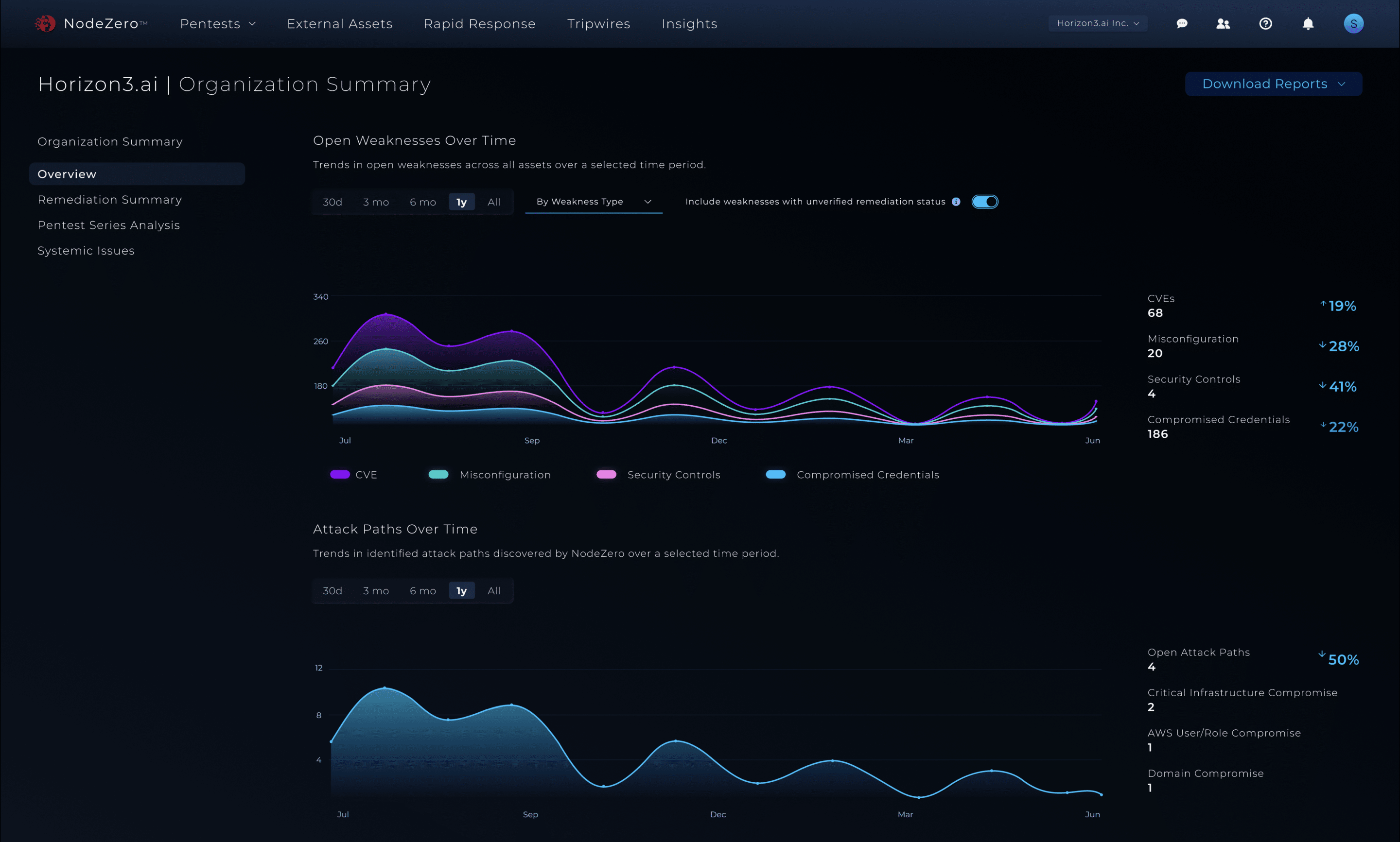
Continuous Pentesting at Any Scale
Scale Beyond Samples, Test Your Entire Enterprise
Don’t just test a small sample of your enterprise—NodeZero scales to test your entire hybrid cloud environment.
Safe for Production
Run Multiple Tests Simultaniously
Schedule Continuous Assesments
The “AI” in Horizon3.ai
NodeZero is an autonomous platform capable of executing self-directed actions to achieve an objective. In pentesting, these objectives include becoming Domain Admin, compromising sensitive data, gaining access to critical systems, and so on. Knowledge graph analytics, inference engines, and learning loops play a key role in ensuring the more pentests NodeZero executes, the “smarter” it gets.
The alternative to our approach is attempting to hardcode every possible attack path using automation. There are far too many variations, and the burden of maintaining automated scripts is significant given how frequently an environment changes. This is why automated pentesting has failed to take off, whereas our autonomous approach, delivered via multi-tenant SaaS, serves customers from the Global 100 to your local hospital.
Learn More About AI for Offensive Security,
Listen to our CEO’s presentation to the National Science Foundation’s ACTION Institute.